New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
CPP: Add query for CWE-266 Incorrect Privilege Assignment #6949
Conversation
cpp/ql/src/experimental/Security/CWE/CWE-266/IncorrectPrivilegeAssignment.cpp
Outdated
Show resolved
Hide resolved
cpp/ql/src/experimental/Security/CWE/CWE-266/IncorrectPrivilegeAssignment.cpp
Outdated
Show resolved
Hide resolved
cpp/ql/src/experimental/Security/CWE/CWE-266/IncorrectPrivilegeAssignment.cpp
Outdated
Show resolved
Hide resolved
My initial thoughts. I'm also interested to see what kind of results we find in real world projects / on LGTM.
cpp/ql/src/experimental/Security/CWE/CWE-266/IncorrectPrivilegeAssignment.cpp
Outdated
Show resolved
Hide resolved
cpp/ql/src/experimental/Security/CWE/CWE-266/IncorrectPrivilegeAssignment.ql
Outdated
Show resolved
Hide resolved
| globalValueNumber(fc.getArgument(0)) = globalValueNumber(fctmp.getArgument(1)) and | ||
| fc.getArgument(0).getValue() != "0" | ||
| ) and | ||
| msg = "not use equal argument in umask and " + fctmp.getTarget().getName() + " functions" |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I'm not convinced this case is right:
- if the
umaskand thechmodvalues are equal, the resulting file permissions are0. This may or may not be what the programmer intended, but0is a very safe permission setting.- I think what we really want is that the argument to
chmodminus the bits fromumaskcontains at least one bit we consider dangerous, e.g. global write permission, suggesting a dangerous setup.
- I think what we really want is that the argument to
- if there's more than one call to
umaskin the program, we don't know whichchmodcalls correspond with whichumaskcall. I'm not sure how common it is in practice to setumaskanywhere other than once at the beginning of the program.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I agree with what you say. (except for using 0 in chmod, I can't figure out why disallow everything for my file)
in the request, I wanted to take a broader look at the cwe-560. and for me the error indicator is the use of the same value in opposite functions. in my opinion, this is a good criterion, devoid of false detection.
but if you insist, I will remove this section from the request
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I see what you mean, even if a resulting permission of 0 is safe, it may indicate a mistake by the programmer. Perhaps we should wait until we run the query on LGTM (after resolving the other questions) and see whether your approach produces good results in practice?
cpp/ql/src/experimental/Security/CWE/CWE-266/IncorrectPrivilegeAssignment.ql
Show resolved
Hide resolved
cpp/ql/src/experimental/Security/CWE/CWE-266/IncorrectPrivilegeAssignment.ql
Outdated
Show resolved
Hide resolved
cpp/ql/src/experimental/Security/CWE/CWE-266/IncorrectPrivilegeAssignment.cpp
Outdated
Show resolved
Hide resolved
cpp/ql/src/experimental/Security/CWE/CWE-266/IncorrectPrivilegeAssignment.cpp
Outdated
Show resolved
Hide resolved
| globalValueNumber(fc.getArgument(0)) = globalValueNumber(fctmp.getArgument(1)) and | ||
| fc.getArgument(0).getValue() != "0" | ||
| ) and | ||
| msg = "not use equal argument in umask and " + fctmp.getTarget().getName() + " functions" |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I see what you mean, even if a resulting permission of 0 is safe, it may indicate a mistake by the programmer. Perhaps we should wait until we run the query on LGTM (after resolving the other questions) and see whether your approach produces good results in practice?
…eAssignment.cpp Co-authored-by: Geoffrey White <40627776+geoffw0@users.noreply.github.com>
…eAssignment.cpp Co-authored-by: Geoffrey White <40627776+geoffw0@users.noreply.github.com>
All looks good to me.
I've started an LGTM run so we can hopefully see some real world results: https://lgtm.com/query/4020291079589842106/
fc.getTarget().hasGlobalOrStdName("umask") and
fc.getArgument(0).getValue() = "0" and
not exists(FunctionCall fctmp |
fctmp.getTarget().hasGlobalOrStdName("umask") and
fctmp.getArgument(0).getValue() != "0"
) and |
cpp/ql/src/experimental/Security/CWE/CWE-266/IncorrectPrivilegeAssignment.ql
Outdated
Show resolved
Hide resolved
…eAssignment.ql Co-authored-by: Geoffrey White <40627776+geoffw0@users.noreply.github.com>
|
Good day @geoffw0 |
For the second case in your query I think this might be sensible. Its possible to report both locations with something along the lines of: This is tricky to do when you sometimes do and sometimes don't have that |
|
if you agree, then I will change the request like this. |
|
Looks reasonable to me. |
|
@geoffw0 |
Running... |
cpp/ql/src/experimental/Security/CWE/CWE-266/IncorrectPrivilegeAssignment.ql
Show resolved
Hide resolved
|
Please don't merge yet, WIP :) |
|
@ihsinme Correct me if I'm wrong, but the vulnerability pattern is valid when functions like |
|
|
|
As I understand from umask documentation this is about a process file mode creation default mask. The file creation (with incorrectly wide file permissions) may happen implicitly during such file operations as Could you please explain me once more why the combination of |
good afternoon @JarLob |
We don't currently have a good model for |
Thanks for the answer. exists(FunctionCall fctmp |
(
(
fctmp.getTarget().hasGlobalOrStdName("fopen") or
fctmp.getTarget().hasGlobalOrStdName("open")
) and
(
not fctmp.getArgument(1).getValue().matches("r%") and
not fctmp.getArgument(1).getValue().matches("O_RDONLY")
)
) and |
|
|
Implements suggestions from github#6949 (comment)

 Formed in 2009, the Archive Team (not to be confused with the archive.org Archive-It Team) is a rogue archivist collective dedicated to saving copies of rapidly dying or deleted websites for the sake of history and digital heritage. The group is 100% composed of volunteers and interested parties, and has expanded into a large amount of related projects for saving online and digital history.
Formed in 2009, the Archive Team (not to be confused with the archive.org Archive-It Team) is a rogue archivist collective dedicated to saving copies of rapidly dying or deleted websites for the sake of history and digital heritage. The group is 100% composed of volunteers and interested parties, and has expanded into a large amount of related projects for saving online and digital history.

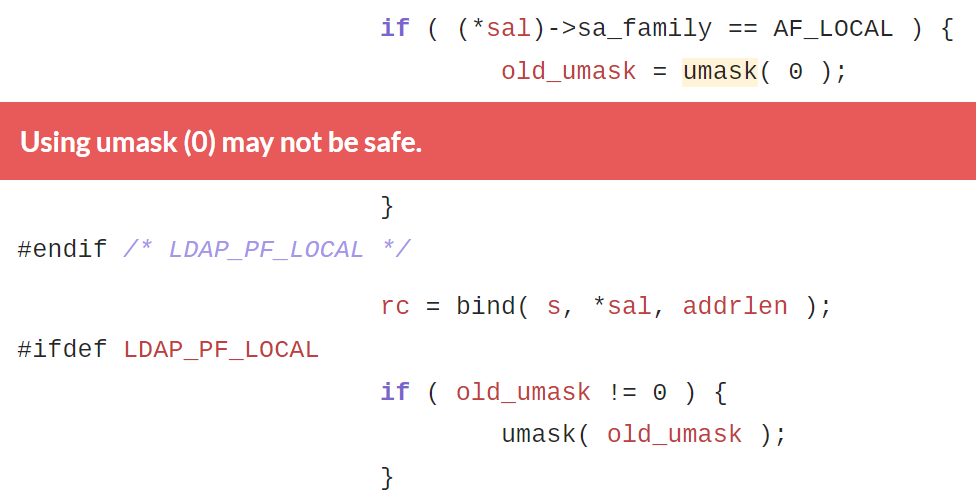
The request looks for situations of incorrect work with setting access rights. Firstly, this is the use of arithmetic to calculate the access mask, and secondly, the use of the same mask in opposite functions, and thirdly, the use of a sufficiently wide mask.
CVE-2013-6412
CVE-2018-14348
CVE-2013-2007
CVE-2001-0859
mydumper/mydumper#451